Introduction
Cybersecurity threats are escalating, and traditional perimeter defenses are no longer sufficient. Zero Trust, the principle of never assuming trust by default, has become the standard. AI-driven adaptive intelligence is now enhancing this model, creating dynamic defenses that respond to evolving risks.
Why It Matters for B2B
Data breaches damage reputation, cost millions, and disrupt operations. In B2B, where sensitive client data and intellectual property are at stake, security is a business-critical priority. Zero Trust with adaptive intelligence ensures every access request is verified and continuously monitored.
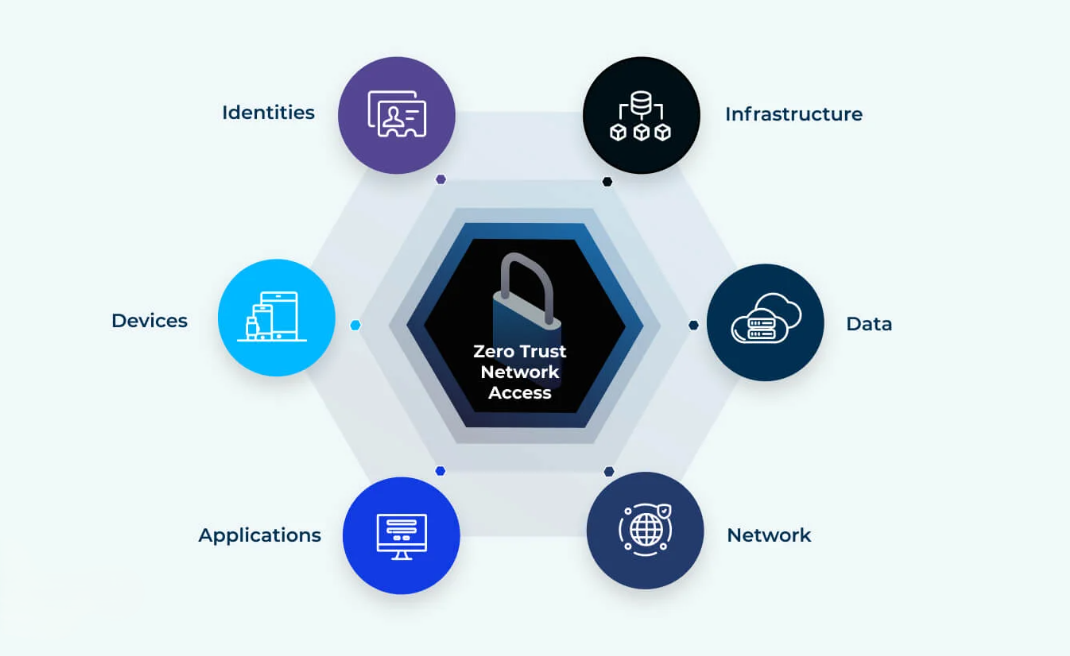
How Adaptive Zero Trust Works
- Identity verification: AI monitors user behavior to detect anomalies.
- Contextual access: Permissions adjust based on device, location, and risk profile.
- Threat detection: Machine learning models identify patterns of malicious activity.
- Automated response: Suspicious behavior triggers immediate containment.
Strategic Guidance for CIOs
- Start with identity and access management as the foundation.
- Layer in behavior analytics for continuous validation.
- Integrate Zero Trust principles across cloud, network, and endpoints.
- Regularly update governance to address new threats.
Risks
Overly strict controls can frustrate users. Balance security with usability by designing adaptive, not static, policies.
Conclusion
Zero Trust with adaptive intelligence transforms security from a static barrier into a living defense system. For B2B organizations, this is not just IT hygiene but a foundation for trust and resilience.